Enable HTTPs for DeviceOn Web Service
Generate Let’s Encrypt certificate using Certbot for DeviceOn.
Let’s Encrypt is a new free, automated, and open source, Certificate Authority.
Certbot is a console based certificate generation tool for Let’s Encrypt. In this recipe, we will generate a Let’s Encypt certificate using Certbot. This certificate will then be deployed for use in the DeviceOn server.
Dependencies:
Port 443 for https needs to be open and available at time of executing certbot.
Certbot needs root access while executing because only root is allowed to bind to any port below 1024.
We will be using our own domain myminio.com as an example in this recipe. Replace with your own domain under your setup.
Steps to Configuration
Step 1: Install Certbot
Install Certbot by following the documentation at https://certbot.eff.org/ Since the DeviceOn Web service is running on Apache Tomcat, please select to “Apache” and “Windows” to downloads Certbot installer.
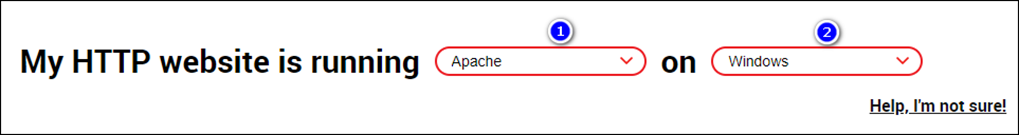
Scrolling down the instruction, you may get the installer package on Step 4. https://dl.eff.org/certbot-beta-installer-win32.exe
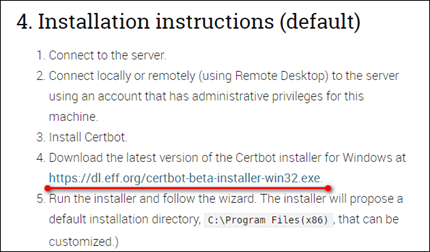
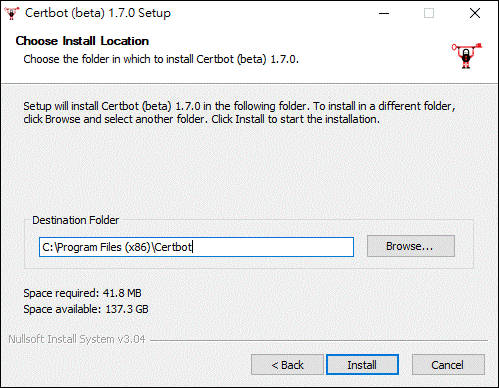
Run the installer and follow the wizard. The installer will propose a default installation directory, C:\Program Files(x86), that can be customized.)
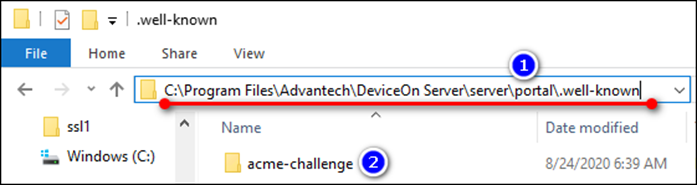
Step 2: Create the folder to authenticate
Create the folder named acme-challenge under <DeviceOn Folder>\server\portal.well-known. If the folder “.well-known” is not exist, please create it manually (via CLI, for example: mkdir).
Step 3: Choose how you’d like to run Certbot
Run the following command to create credential files and enter your website information. The domain name(s) should input yours and the webroot to \DeviceOn Path\server\portal\
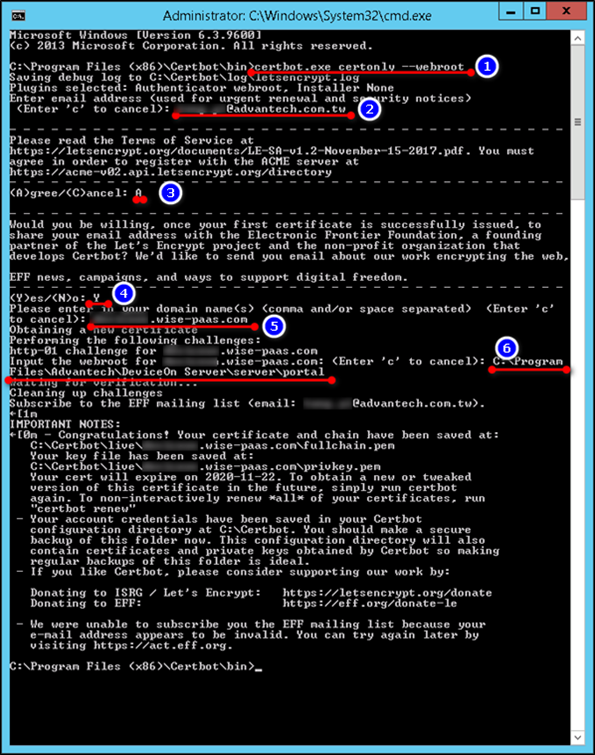
Step 4: Install your certificate
You’ll need to install your new certificate in the configuration file or interface for your webserver. Certificates are located in C:\Certbot\live[certificate_name], where [certificate_name] is the name of your certificate (usually the first domain if the –cert-name flag has not been used on the certonly command)
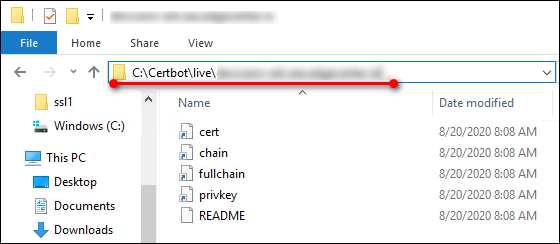
Step 5: Install your certificate on DeviceOn Web Services
Open the server.xml on text editor tool that located in the \DeviceOn Path\tomcat\conf\
Please append the new XML attribute 'Connector' within the 'Service' tag, and provide the certification path (lines 26 to 28) that was generated during Step 4.
Step 6: Restart DeviceOn web services (Tomcat_IoT) to reload the configuration
Step 7: Replace the certificate files that in the websockify folder.
Step 8: Enable to automatic renewal
Create a batch file named restartTomcat.bat which content as below

Copy the batch file into C:\Certbot\renewal-hooks\post\
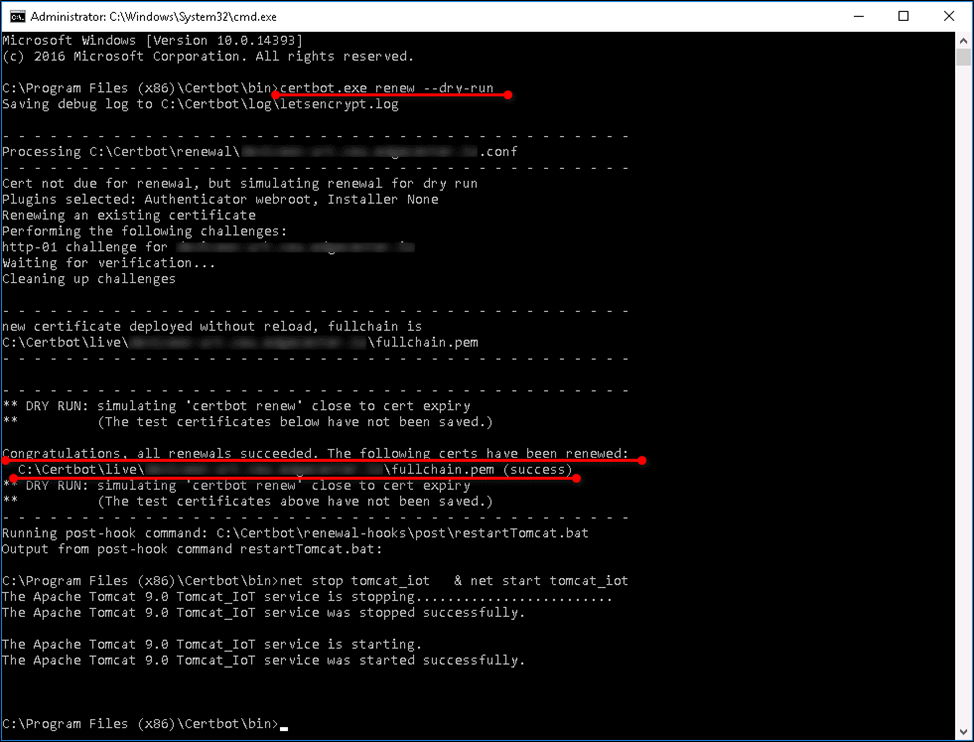
Step 9 (Optional): Test automatic renewal, please run the following command
Step 10 (Optional): If you get all renewals succeeded, it means your configuration is correct.
Step 11: Turn Windows firewall on inbound port 443 for your HTTPS, and make sure your network security rules allow.
Step 12: Use the Server Configuration tool to update your web server configuration. For instance, if your previous web service URL was http://<YOUR_DNS>:8080, change it to https://<YOUR_DNS>.

After making the update, click 'Apply' and then restart the Tomcat service.

Last updated